前言
由于之前陆陆续续添置了不少电子设备,以及更换 ISP 的原因,机架上连了5台设备,每台各负责一点点事情,不管是配置还是调试都很麻烦。再加上旧路由器不能很好同时处理千兆 NAT 和 VLAN,于是最近入手了一台 RB4011iGS+5HacQ2HnD-IN,把这一堆乱七八糟的设备统统换掉。主要需求有三点:
- 划分2个 VLAN,一个内部网络,一个访客网络。
- IPv4 和 IPv6 双栈接入。
- 因为路由器直接暴露在 Internet 上了,所以防火墙一定要配好,包括 VLAN 之间的访问也是靠防火墙来控制的。
端口及 VLAN 配置
MikroTik 家的路由器的二层交换配置是比较不统一的。受限制于不同产品的硬件,想要完全利用硬件交换,不同的型号在 Bridge 的设定上都略有不同。建议到 MikroTik Wiki: Switch Chip Features 页面查询具体型号的配置方法。由于我的大部分内网流量还是要过 CPU 三层路由的,所以我没有在这一点上做特别优化,反正 RB4011 的性能够用。我这里以两个 VLAN,每个 VLAN 里各有一个 Ethernet 接口和一个 Wireless 接口为例。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| /interface wireless
# 修改内部无线网络接口 VLAN ID 为 900
set [ find default-name=wlan1 ] name=wlan5g vlan-id=900 vlan-mode=use-tag <...其他参数省略...>
# 增加访客无线网络接口 VLAN ID 为 200
add master-interface=wlan5g name=wlan5g_guest vlan-id=200 vlan-mode=use-tag <...其他参数省略...>
/interface bridge
# 新建网桥,注意这个网桥自己的 VLAN ID 我们用不到,所以填什么都可以
add frame-types=admit-only-vlan-tagged ingress-filtering=yes name=LAN protocol-mode=none pvid=900 vlan-filtering=yes
/interface bridge port
# 把两个无线和两个有线都加进桥
add bridge=LAN frame-types=admit-only-vlan-tagged ingress-filtering=yes interface=wlan5g pvid=900
add bridge=LAN frame-types=admit-only-vlan-tagged ingress-filtering=yes interface=wlan5g_guest pvid=200
add bridge=LAN frame-types=admit-only-untagged-and-priority-tagged ingress-filtering=yes interface=ether2_nas pvid=900
add bridge=LAN frame-types=admit-only-untagged-and-priority-tagged ingress-filtering=yes interface=ether3 pvid=200
/interface bridge vlan
# 配置桥的 VLAN 转发表
add bridge=LAN vlan-ids=900 tagged=LAN,wlan5g untagged=ether2_nas
add bridge=LAN vlan-ids=200 tagged=LAN,wlan5g_guest untagged=ether3
/interface vlan
# 在桥上新建两个 VLAN 接口,之后 IP 地址以及 DHCP 服务器就分配给它们
add interface=LAN name=LAN.guest vlan-id=200
add interface=LAN name=LAN.trusted vlan-id=900
/ip address
# 分配 IP
add address=192.168.9.1/24 interface=LAN.trusted network=192.168.9.0
add address=192.168.2.1/24 interface=LAN.guest network=192.168.2.0
|
DHCP 配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| # IPv4 DHCP 客户端
/ip dhcp-client
add !dhcp-options disabled=no interface=ether1_ont use-peer-dns=no use-peer-ntp=no
# IPv4 DHCP 服务器
/ip pool
add name=dhcp_trusted ranges=192.168.9.200-192.168.9.250
add name=dhcp_guest ranges=192.168.2.200-192.168.2.250
/ip dhcp-server
add address-pool=dhcp_trusted disabled=no interface=LAN.trusted name=dhcp_trusted
add address-pool=dhcp_guest disabled=no interface=LAN.guest name=dhcp_guest
/ip dhcp-server network
add address=192.168.2.0/24 gateway=192.168.2.1
add address=192.168.9.0/24 gateway=192.168.9.1
# DHCPv6 获取前缀
/ipv6 dhcp-client
add add-default-route=yes interface=ether1_ont pool-name=ipv6_ont_pool request=prefix use-peer-dns=no
# 配置 IPv6 SLAAC
/ipv6 address
add from-pool=ipv6_ont_pool interface=LAN.trusted
add from-pool=ipv6_ont_pool interface=LAN.guest
|
IPv4 防火墙配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| /ip firewall nat
add action=masquerade chain=srcnat ipsec-policy=out,none out-interface=ether1_ont comment="NAT"
/ip firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=input comment="非内部网络不可访问路由器" in-interface=!LAN.trusted
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related
add action=accept chain=forward comment="defconf: accept established,related, untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from ether1 not DSTNATed" connection-nat-state=!dstnat connection-state=new in-interface=ether1_ont
add action=drop chain=forward comment="其他 VLAN 不可访问内部 VLAN" out-interface=LAN.trusted
add action=drop chain=forward comment="访客 VLAN 不可访问除 Internet 以外的网络" in-interface=LAN.guest out-interface=!ether1_ont
|
IPv6 防火墙配置
1
2
3
4
5
6
7
8
9
10
11
12
13
| /ipv6 firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="允许所有 ICMPv6 报文" protocol=icmpv6
add action=accept chain=input comment="允许 DHCPv6 前缀分配报文" dst-port=546 protocol=udp src-address=fe80::/16
add action=drop chain=input comment="非内部网络不可访问路由器" in-interface=!LAN.trusted
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=out,ipsec
add action=accept chain=forward comment="defconf: accept established,related, untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=forward comment="允许访问互联网" out-interface=ether1_ont
add action=drop chain=forward comment="拒绝所有其他转发流量"
|
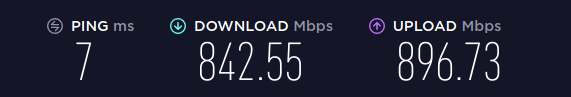
测试总结
配置完了以后我对这一套设备还是挺满意的。在 IPv6 没有 Fasttrack 只能纯 CPU 转发的情况下,双向同时 900Mbps 测速,CPU 占用在 80% 左右。发热也没有什么感觉,反正平时一直丢角落里,估计整台机器最烫的部分就是那个 SFP+ 的万兆收发器了吧。


